Due to pressure of local regulatory compliance issues and/or corporate governance demands there is a growing awareness of Governance Risk and Compliance among executive management. Use CSI tools to document all (SOx) governance principles on the fly, test and get insight in the status of the current access governance and remediate the risks.
Get clean and compliant with documenting and testing
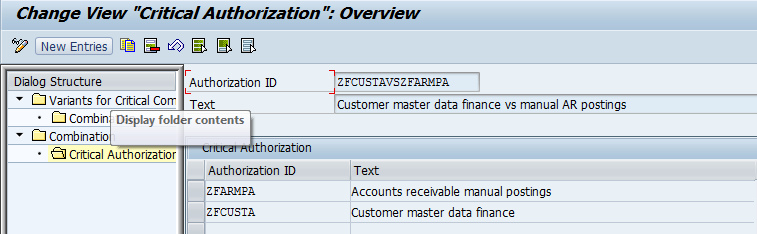
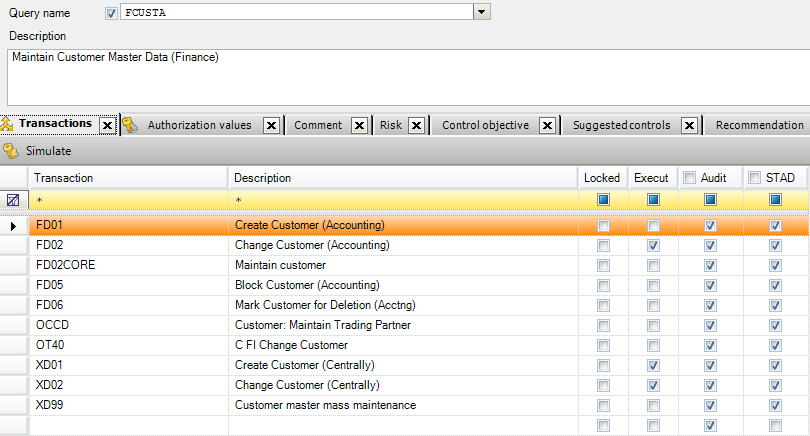
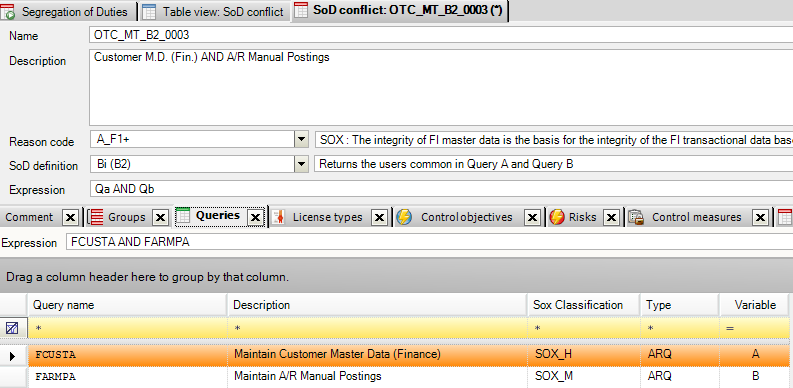
CSI Authorization Auditor comes with a pre-defined audit and segregation of duty ruleset with over 400 SoD conflicts. This rule set can be fully fine tuned to the organizations’ needs, like custom authorizations. The rule set can be centrally adjusted with all organizational values like company code, plants, sales organizations, et cetera.
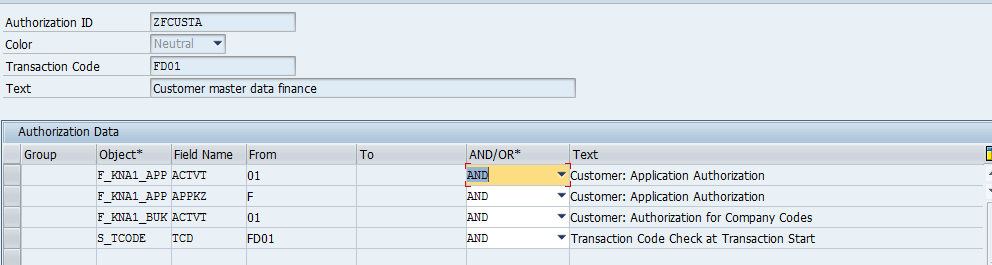
The organizations’ business control framework with all processes, sub processes, risks (incl. all risk information like risk indicators, descriptions, ..), control objectives, control measures with norms, SoD conflicts, et cetera is documented in CSI Authorization Auditor on the fly.
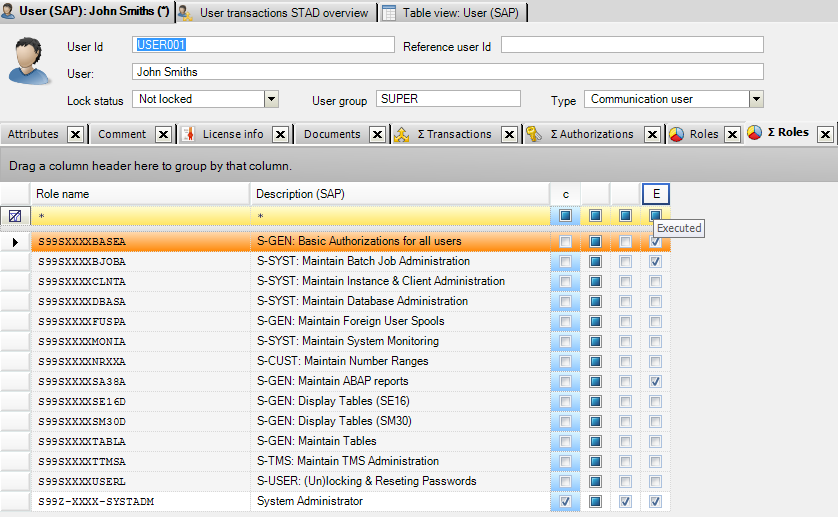
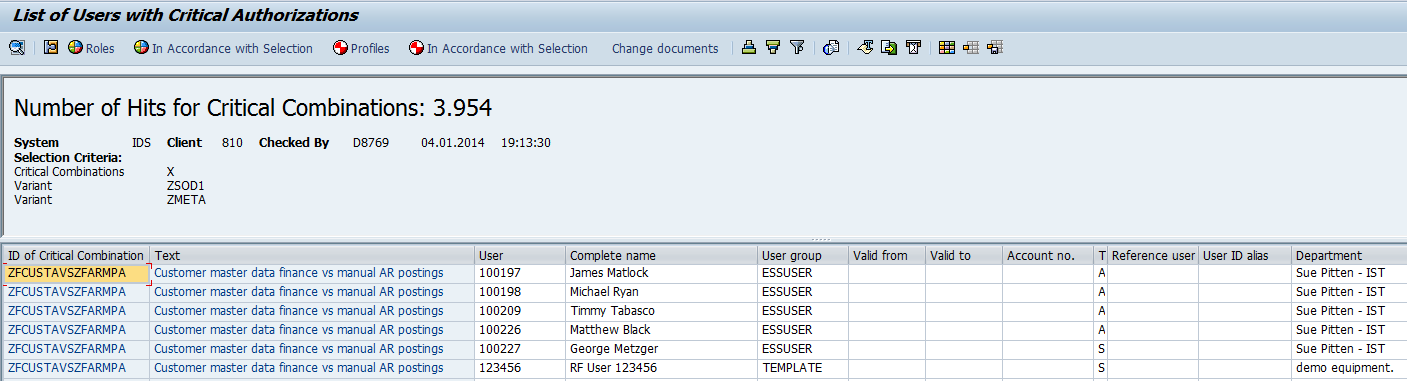
Who can access which data and did they execute it? Who has broad access through different stages of the process and therefore segregation of duty (SoD) conflicts and did they execute all activities within the conflict? Are all the backdoors secured? Are there inconsistencies in roles, user role assignments or in the rule set? Are the implemented compensating control measures taken care of? CSI Authorization Auditor gives the answer using a multi layered analysis.
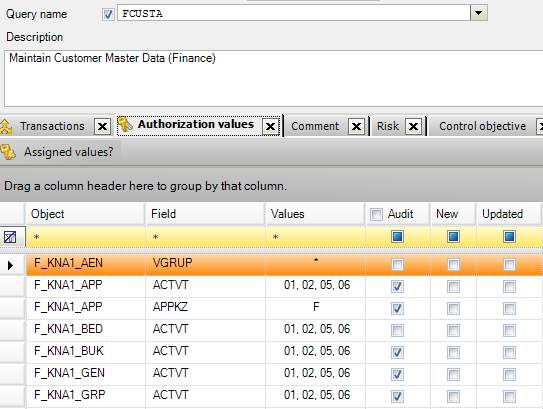
The customizing of the SAP system is checked automatically against the pre-defined control measure norms to speed up the testing process in CSI Authorization Auditor.
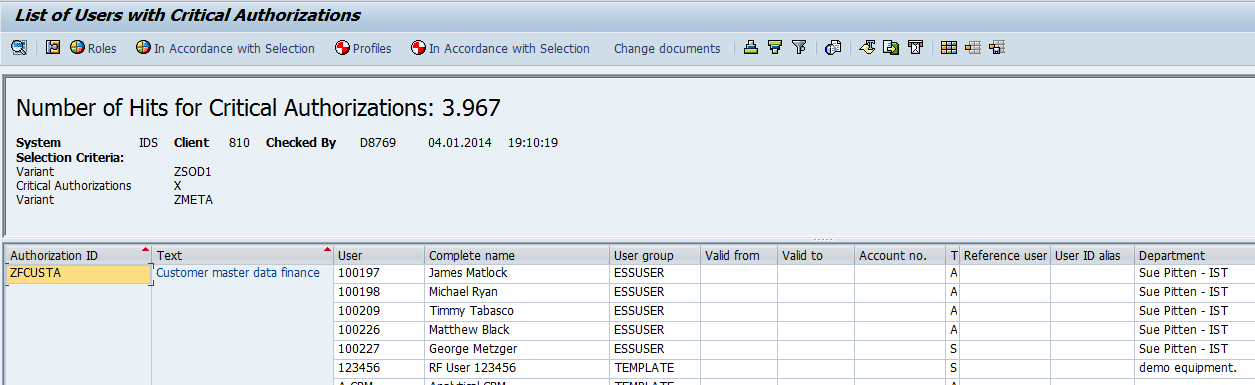
All test results are stored in CSI Authorization Auditor, accompanied with traffic lights indicators to give insight in mitigated and remaining risks.
When the insight in the risks is clear, it is time for the next step, mitigation and remediation. Mitigating critical access risks and SoD conflicts can be done via:
- Authorizations changes on role level
- Authorization changes on user level
CSI Authorization Auditor gives insight how to mitigate the SoD conflicts based on the executed transaction information and the norm information that the business can maintain directly and by themselves.
Once the insight is there, it might be necessary to make changes in the current set up of the authorizations (roles, role assignments,…) to get solid access governance. This is fully supported by CSI Role Build & Manage with features like automatic role building and deriving of roles (using reverse engineering), consistency checks and pre SOD check of the roles. CSI Role Build & Manage speeds up the phase to get clean & compliant.
Not all risks can be mitigated via authorization changes, some risks need to be mitigated by implementing compensating controls. The compensating controls are defined in CSI Authorization Auditor and will be part of the testing cycle. All test evidence for the compensating controls are stored in CSI Authorization Auditor.
Stay clean and compliant
Once the access governance is clean and compliant the next step will be “stay clean & compliant”; keep compliant access governance using Automated Request Engine that provides functionality like pre SOD checking and workflow integration for all authorization and user requests.
Granting users temporary broad access rights is handled and monitored with CSI Emergency request. This tool also has the unique functionality to get insight in the changes that were made for critical info types. This insight is required by law in countries like Germany.
Prove you are complaint
Monitor and test the risks and controls and document all the evidence in CSI Authorization Auditor to prove you are compliant. The organization’s business control framework is documented in one central place and includes all test evidence.
The audit committee can use CSI Authorization Auditor stand alone with its own audit rule set to check the authorization structure independently.
Changes to the rule set in CSI Authorization Auditor and roles in CSI Role Build & Manage are logged automatically.
(C) Meta Hoetjes 2015 CSI Authorization Auditor and CSI Role Build and Manage are registered trademarks by CSI Tools bvba www.csi-tools.com