1. What do we need to do to get in control?
First, get insight in the status of the current access
governance: “Who can access which data and did they execute it? Who has broad
access through different stages of the process and therefore segregation of
duty conflicts and did they execute all activities within the conflict? Are all
the backdoors secured? Are there inconsistencies in roles, user role assignments
or in the rule set?” The questions are clear, but how to get to the answers?
1.1 Define overview and rule set with functionality and SOD conflicts that are business critical
First you have to define a company specific overview of
all the functionality and Segregation of Duty (SoD) conflicts that are business
critical. Once this overview is there, it must be translated into SAP technical
authorizations. SAP authorization knowledge is needed for this translation and
it will take many man hours to search and find the correct authorizations and
transactions.
How CSI
Authorization Auditor® 2014 can help in this step.
CSI Authorization Auditor® 2014 comes with a pre-defined rule set containing over
400 SOD conflicts and the critical functionality are already translated into
authorization values and transactions (queries). This rule set is a real time
saver. Instead of defining SOD conflicts from scratch, use the predefined SOD
conflicts and decide which conflicts are critical for the organization.
1.2 Analyze the authorization concept
The bad news about analyzing the SAP authorization concept
is that SAP does not support this process in their standard SAP system with
user friendly reports or tools. The authorization data is stored in tables in
the SAP database. Analyzing them manually is not recommended. It is a manual
(returning) job, needs to be done in the correct way and is very time
consuming. Problems with manual analyzing are:
·
Mistakes are very easy to make because of the
numerous reports that needs to run with the correct credentials. If a mistake
is made unnoticed people are looking at incorrect data that leads to incorrect
actions.
·
Extracting the data is very difficult and can
result in SAP system overloading and errors.
·
Only a limited scope can be taken into account
because analyzing all the company critical functionality and SOD data just
takes too much time.
·
SAP authorizations or even the rule set may
change regular; therefore the check needs to be done recurring.
·
Not all aspects of access governance can be
taken into account. SAP systems have many backdoors that lead to critical data.
With manual analyzing these backdoors cannot be taken into account.
·
Company specific organizational levels are very
difficult to include and maintain in the analysis.
·
Comparing results over periods is a separate
activity that needs to be done as well.
·
Once the results are reported, an additional
manual analysis needs to be done if SoD conflicts and access to access to
critical functionality by users must be adjusted.
How CSI
Authorization Auditor® 2014 can help in this step
Using CSI Authorization Auditor® 2014 will cut back the
manual analyzing efforts that will take days (if not weeks) and reduce them to
a couple of hours (and maybe less). CSI Authorization Auditor® 2014 helps
getting insight in a fast and easy way of the current access governance. Who
can access which data and did they execute it? Who has broad access through
different stages of the process and therefore segregation of duty conflicts and
did they execute all activities within the conflict? Are all the backdoors
secured? Are there inconsistencies in roles, user role assignments or in the
rule set? CSI Authorization Auditor® 2014 gives the answer using a multi
layered analysis. The analysis will be done outside the SAP system and the data
extraction can be scheduled. Therefore there will be no workload on the SAP
system. Dashboards, reports and trending overview are standard available in CSI
Authorization Auditor® 2014.
2. What do we need to do to stay in control?
Once the access governance is clean and compliant the next
step will be “stay clean & compliant”; Define the Business processes, risks
and controls. Monitor the security concept and store the evidence. This can be
done manually (for example in Excel), but once again will be very time
consuming. Checks like the correct configuration table values need to be
checked in the SAP system manually and evidence needs to be stored.
How CSI
Authorization Auditor® 2014 can help in this step
Define the Business processes, risks and controls on the
fly. Monitor the security concept and store the evidence in CSI Authorization
Auditor® 2014. Stay compliant with your clean security concept using CSI
Authorization Auditor® 2014’s user request functionality with pre SOD checking
for the authorization and user changes. Monitor the risks and controls and
document all the evidence in CSI Authorization Auditor® 2014 to prove you are
compliant.
The audit committee can use CSI Authorization Auditor®
2014 stand alone with their rule set to check the authorization structure
independently. Changes to the rule set in CSI Authorization Auditor® 2014 are
logged automatically.
Advantages CSI tooling:
- CSI Authorization Auditor® 2014 covers all aspects of access governance
- The audit committee can use CSI Authorization Auditor® 2014 PC based. Only they have access to the audit rule set and perform independent audits.
- Documenting the security process can take a long time. CSI Authorization Auditor® 2014 can simultaneous implement and document the business process with risks and controls step by step. Add any information about the security process CSI Authorization Auditor® 2014 and make changes on the fly. Use CSI Authorization Auditor® 2014 to document the security process in a fast way.
- Fast implementation time
- Clear overview of SOD conflicts and how to solve them, results are on different views expandable.
- A sequence of dialog boxes leads the user through a series of well-defined steps (wizard). Tasks that are infrequently performed are easier to perform using the wizard. CSI Authorization Auditor® 2014 supports reporting the right results in the fastest way. Because of the use of the new interface and wizards, users are guided through the application with additional information on the screen, this reduced training effort enormously.
- CSI Authorization Auditor® 2014 comes with a large number of useful reports and dashboards. Is the report or dashboard not fitting the business requirements? Customizing is also possible to create new ones. End-users can define their own grouping of all data shown on screen and every view can be exported to different formats like xlsx, xml, pdf and accdb.
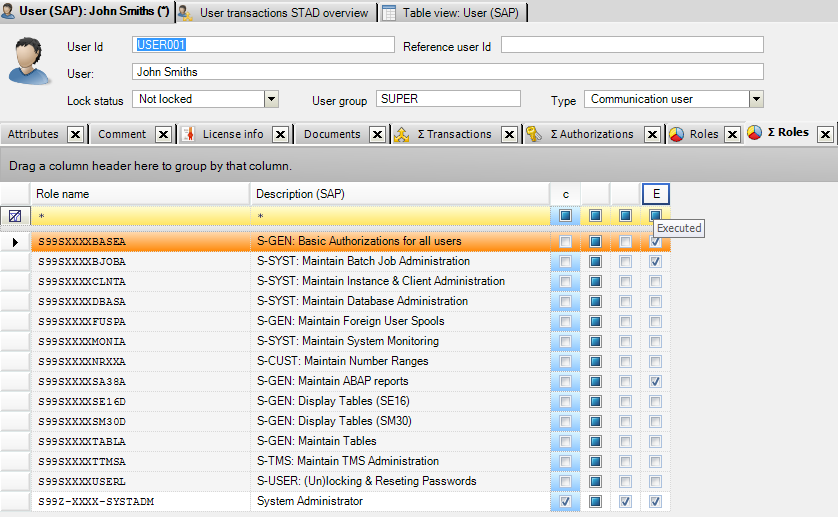
- All audit reports have the full causing information available with insight how these access rights are assigned to users. On every level an indication is given whether or not the user needs the role based on transaction usage information.
- CSI Authorization Auditor® 2014 gives a clear overview about the usage of SAP licenses. Reduce expensive license costs and pay only for the licenses and authorizations that are really being used.
- Messages can be distributed according the RASCI matrix. Implement the organizations’ responsibility assignment matrix to automate the security task messages. People are informed automatically when they need to perform a task in the security process.
- Work simultaneous with multiple users on the same data to see the results in a clear overview, no more manual report distribution.
- CSI Authorization Auditor® 2014 uses two databases; an application database and an archive database. All original SAP data and all previously produced audit results are saved in the archive. Previous audit result are immediately available if needed, the current audit results can be compared in detail with previous audit results.
- New reports and dashboards make it possible to compare the audit results over periods. See if the security concept is improving.
- Analyze the correctness of role assignments with the use of role information and statistical data from the SAP system. CSI Authorization Auditor® 2014 also gives a clear view if access rights are accumulating in the security concept. This information can be used to clean up the authorization concept to get compliant.
- All analyses are done separately on authorization level and transaction code level including executed information. The differences between these results give authorization managers an immediate insight of inconsistencies in the SAP roles and/or audit rules and/or in the access governance process.
- Useful user information can now be found in CSI Authorization Auditor® 2014: which roles are assigned to the user, which transactions a user can (and did) execute (even if the transactions are already removed) and which authorizations are assigned to the user in his/her user buffer.
- CSI Authorization Auditor® 2014 logs all changes made to the rule sets.
(C) Meta Hoetjes 2014
CSI Authorization Auditor and CSI Role Build and Manage are registered trademarks by CSI Tools bvba
www.csi-tools.com